Twitter Trademark and Content Display Policy
This policy is designed to help you use our brand and assets, including our logo, content and trademarks without having to worry about negotiating a separate agreement with us or talking to our lawyers. If you’d like to make any use of our marks that is not covered by this document, you must contact us at trademarks at twitter.com and include a visual mockup of intended use.
Using the Twitter brand and trademarks∞

Twitter’s marks include, but are not limited to, the Twitter name, logo, Tweet, Twitter bird, and any word, phrase, image, or other designation that identifies the source or origin of any of Twitter’s products.
Do not modify or alter the marks or use them in a confusing way, including suggesting sponsorship or endorsement by Twitter, or in a way that confuses Twitter with another brand.
Downloads
Usage guidelines
Do:
- Use our official, unmodified Twitter bird to represent our brand.
- Make sure the bird faces right.
- Allow for at least 150% buffer space around the bird.
Don't:
- Use speech bubbles or words around the bird.
- Rotate or change the direction of the bird.
- Animate the bird.
- Duplicate the bird.
- Change the color of the bird.
- Use any other marks or logos to represent our brand.


Promoting your Twitter account∞
Do:
- Use one of the Twitter buttons as a link to your account online.
- Use one of the Twitter bird logos with your @username nearby in print.
- Write out Follow us on Twitter with your @username nearby when you’re unable to show the Twitter bird.
Don't:
- Manipulate the Twitter bird.
- Use any other artwork from our site, such as the verified badge.
- Create your own buttons or images using our logos unless technically necessary, such as in signature bars. If you do, use this resized version of the Twitter bird.
Twitter brand in advertising or marketing materials∞

Do:
- Use the Twitter bird to show that your product or device is compatible with Twitter.
- Show the Twitter bird in front of your #hashtag or @username the same size as the text.
- Make sure that if mentioning "Tweet," you include a direct reference to Twitter (for instance, "Tweet with Twitter") or display the Twitter brand or trademarks with the mention of "Tweet."
See the section regarding Displaying Tweets and other content from Twitter if using Tweets or building a microsite.
Don't:
- Display the Twitter brand or trademarks larger than your own marks.
- Use the Twitter brand or Tweet mark to refer to any service other than Twitter.
Merchandise and manufactured items∞
Please note that we generally don’t permit use of our marks on merchandise.
Do:
- Use the Twitter bird on your product packaging with your @username to let customers know you’re on Twitter. The Twitter bird should be the same size as your @username and should not be larger than your own branding.
Don't:
- Use the Twitter name, the Twitter bird, Tweet, or any other confusingly similar marks on any apparel, product, toy, or any other merchandise.
Naming applications, products, or domains∞
Do:
- Name your website, product, or application with something unique.
Don't:
- Use Twitter in the name of your website, application or product.
- Use just "Tweet" or "Tweet" with a simple letter or number combination (for example, 1Tweet, Tweet, Tweets).
- Register a domain containing twitter, misspellings, transliterations or similar variations thereof.
- Apply for a trademark with a name including Twitter, Tweet, the Twitter bird, transliterations or similar variations thereof.
- Use Tweet in the name of your application if used with any other service.
Visual design of your website or application∞
Do:
- Design your site with unique branding and logos.
Don't:
- Copy our look and feel, as this could create user confusion.
Books or publications about Twitter∞
Do:
- Make sure the title of your book or publication makes clear that it's about Twitter, and not by Twitter. For example, "Learning how to 'X' on Twitter" is appropriate, whereas "The Twitter guide to 'X'" is not.
- See the section regarding using content from Twitter if displaying Tweets.
Don't:
- Use the Twitter Bird on your cover or in your title.
- Use the word Tweet to refer to services other than Twitter.
Displaying Tweets and other Twitter content∞
When showing a Tweet online, offline, or in broadcast, you shouldn’t confuse users by including actions from other social platforms. Any Tweets displayed must be real, from real accounts, and in some cases as listed below, approved by the author.
In Broadcast
For full broadcast guidelines, please see our resource on our Help Center.

Do:
- Make sure Tweets shown on air include name, @username, and unmodified Tweet text with the Twitter bird nearby.
- Display the associated Tweet and attribution with images or media. Multiple-image galleries or scenic integrations should be marked clearly as 'from the Twitter service' and provide the associated #hashtag or @username.
- Show the Twitter bird before #hashtags and @usernames to maximize engagement. The bird should be the same size as the text.
Don't:
- Delete, obscure, or alter the identification of the user. You may show Tweets in anonymous form in exceptional cases such as concerns over user privacy.
- Confuse broadcast with advertisements, which require approval from the Tweet author.
Online (Developers and microsite campaigns)
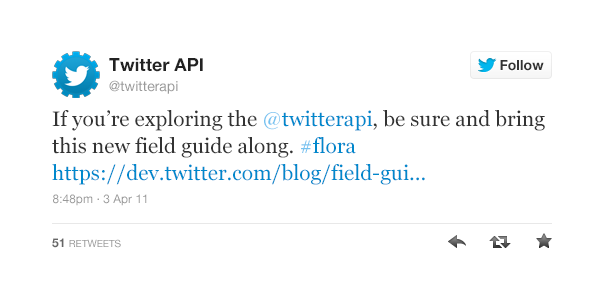
- Follow our Display Policy for Online Use or use Embedded Tweets.
- Display the associated Tweet and attribution with images or media. In multiple-image galleries or scenic integrations, Tweets can be displayed via hover or touch interaction.
- Follow our Developer Rules of the Road and Terms of Service.
- See our rules on Contests on Twitter and Spam and Automation.
- See the section on showing the Twitter trademarks.
- If your microsite is an advertisement and you’re curating content, make sure Tweets are real, from real accounts, and approved by the author.
Offline (Static uses and publications)

- Show name, @username, unmodified Tweet text, and the Twitter bird nearby, as well as a timestamp.
- If displaying Tweets, make sure they are real, from real accounts, and that you have permission from the author when necessary.
- Display the associated Tweet and attribution with images or media.
- If showing screenshots, only show your own profile page, the @twitter page, the Twitter 'About' page, or a page you have permission from the author to show.
- See the section on displaying the Twitter trademarks.
Other things to know about the Twitter trademarks∞
- Please do not use the Twitter marks in your avatar or the background of your Twitter page.
- Please remember to capitalize the T in Twitter and Tweet.
By using the Twitter marks you agree to follow the above as well as our Terms of Service and all Twitter rules and policies. Twitter reserves the right to cancel, modify, or change the permission in this policy at any time at its sole discretion. For further information about use of Twitter's name and trademarks, please contact trademarks at twitter.com.




Comments
Post a Comment
share your thoughts ....