Requirement to hack someone's Facebook account:
1. Victim (whose Facebook account password you wanna hack) should be on Facebook.
2. Create four to five fake Facebook accounts(three are sufficient but one more for bonus). I will advice you that create accounts with girl names and put an awesome girls photograph. Fill the basic profile.. Why i am saying create account with Girl names is just because Hungry boys accepts girls friend request without any delay. And if you know the person personally then create account with names of his near ones and say that you have created new profile so add you as a friend. Note all the three to four fake accounts should not be friends or any relationship with each other.
3. Most important requirement you need to add all above three account to the friends list of victim whose Facebook account you want to hack. Above method will be helpful for that :P.
3. At least two web browsers. So that one can be used as recovery purpose and one for viewing codes.
So guys i hope you all are clear with requirements to hack Facebook account password. Now lets hack someone's Facebook account password practically to show that hacking Facebook account really works.
Steps to hack any Facebook account password in less than 10 minutes 100% working hack with practical example:
In these steps i am hacking the Facebook account password of user whose email ID is ajay2008singh@gmail.com (its mine own account but fake one that i use for testing hacks).
1. Open the Facebook in your web browser.
2. Now Click on Forgot your password? Now a new tab will open something like this. In the email box give the email ID 'ajay2008singh@gmail.com' and press enter or click on search button as shown in below snapshot..
 |
| Learn How to hack Facebook account password Snapshot 1 |
3. Now after Clicking on search you will get an Captcha verification. Type the words displayed and press enter.
4. Now You have reached to the screen Where Facebook gives the search results of the identity of previous step. There you will see button saying "This is my account" just click on that as shown below in snapshot:
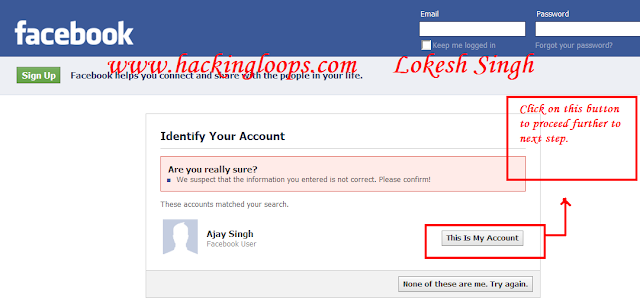 |
| Hacking Facebook account password snapshot 2 |
5. Now you have reached to the below Facebook password recovery screen as show below:
 | ||
| Hack Facebook Password recovery snapshot 3 |
Now Click on "No Longer have access to these?" hyperlink to go to next step.
6. Ahhah... It sounds great everything going smoothly... So friends after following step 5 you will reach below page that ask you Enter your new email ID for contact. Its most important as password reset request after submitting codes will be received on this.. Below is snapshot of screen 4:
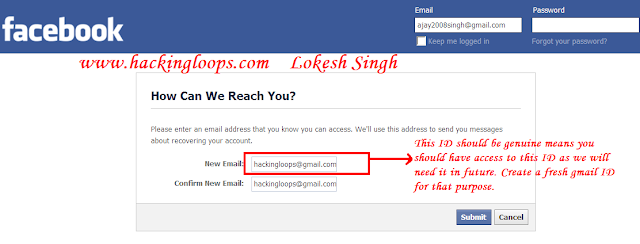 |
| How to hack facebook account or passwords snapshot 4 |
7. After submitting you will have either of two situations:
a. First One will be recover your account with friends.
b. Answer the security question if victim has set the security question.
Now what...
Oops.. he has set the security question and i dont know the answer... What should i do??.....Scared ... nopes...worried... nopes... Let's enter wrong answer to his security question three times... Omg... WTF has happened I am redirected to the First option " Recover your account with your friends" .. :P .. I love explain things in dramatic manner so that reader also get interest. :P
8. Now you are at screen saying " Recover your password using your friends" as shown below in snapshot.
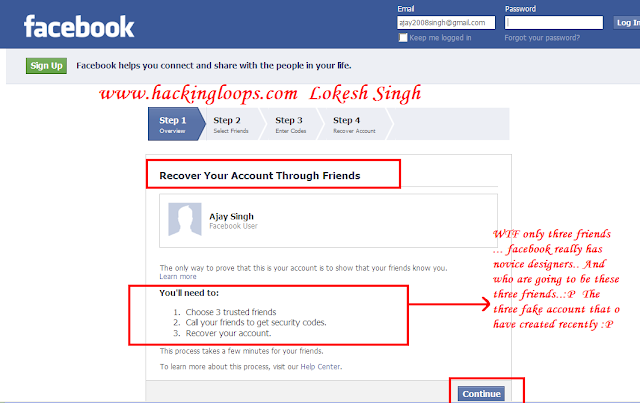 |
| 100% working practical facebook account password hack snap 5 |
9. Just click on continue and select the three trusted friends :P The three fake accounts that we have created for him to hack his account....:P..
You can also perform this hack by making your friends participate to hack someones account...Now select three accounts one by one as one... Below is the screen shot showing that i have selected three friends whom i am sending codes.
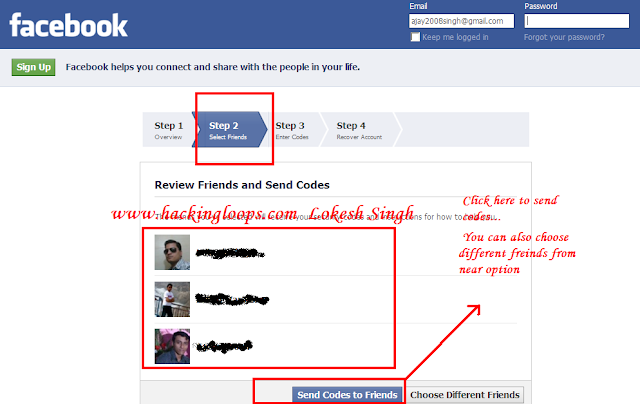 |
| Facebook account hacking final snapshot |
10. Foow....Oops.. I got all the three codes....Below is the screen where you will enter those three codes that you have received...
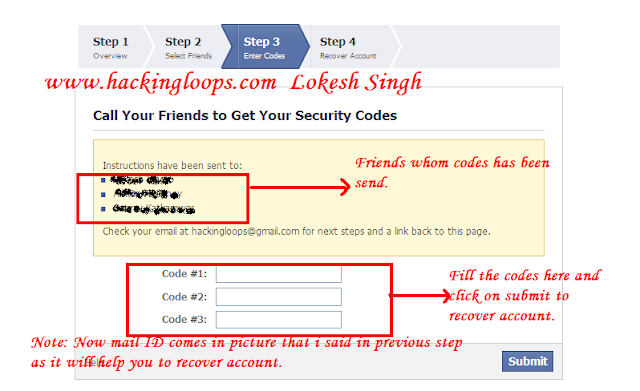 |
| Filling confirmation codes for hacking facebook account |
So guys we are done.... Fill the codes into boxes that you have received into you messages in Facebook and on email if feed is subscribed.
Click on submit now it will ask you to validate your email account that you have filled in Step number 6. That email should be genuine as you will receive recovery email on that email account only...
That finishes my Practical example with complete clear snapshots to hack Facebook account password..
Read more: http://www.hackingloops.com/2011/07/how-to-hack-facebook-account-password.html#ixzz2VDRV61sv
Comments
Post a Comment
share your thoughts ....